
In Security Systems, Intrusion Prevention is fundamental. Common Intrusion Detection methods include:
1. Video Surveillance and Intelligent Analysis
CCTV Systems: Surveillance cameras monitor specific areas in real-time and record video to identify potential intrusions. By integrating Artificial Intelligence (AI) and Video Analytics, the system can automatically detect suspicious activities such as unauthorized entry, loitering, or unattended objects.
Intelligent Video Analytics: AI-powered video analysis identifies Intruders, movement patterns, and object displacement, reducing false alarms while improving detection accuracy.
For example, combining CCTV Systems with Facial Recognition and Behavior Analysis allows for quick identification of unauthorized individuals or suspicious activities.
2. Access Control Systems
Access Control Systems regulate entry to restricted areas using authentication methods such as Keycards, PIN Codes, Fingerprints, Facial Recognition, or Registered User Credentials.
Identity Verification: If an unauthorized person attempts to bypass the system, an alert is triggered immediately.
Alarm Integration: In case of unauthorized access attempts (e.g., Forced Entry, Unauthorized Card Usage), the system can activate alarms and link with Video Surveillance for further monitoring.
3. Intrusion Detection Systems (IDS) and Alarm Systems
IDS and Alarm Systems monitor designated areas for unauthorized access and trigger alerts upon detecting anomalies.
Infrared Sensors: Installed at entry points or key locations, these sensors detect heat changes when an Intruder is present and activate alarms.
Microwave Sensors: These sensors detect movement based on Microwave Signal Fluctuations within a designated area.
Vibration Sensors: Installed on Doors, Windows, and other vulnerable entry points, these sensors trigger alarms upon detecting Forceful Entry Attempts or break-ins.
4. Physical Intrusion Prevention (Fences and Protective Barriers)
Fences and Protective Barriers serve as the first line of defense, typically installed around Buildings, Factories, Warehouses, and other facilities to prevent unauthorized access.
High-Voltage Electric Fencing: This deters Intruders by delivering an Electric Shock, often used in High-Security Areas.

Fence and Ground Vibration Sensors: Embedded in Fences or Buried Underground, these sensors detect Climbing, Cutting, or Tampering Attempts, triggering alarms accordingly.
5. Infrared and Laser Intrusion Detection
Infrared Sensors: Detect Intruders by sensing Heat Radiation. When an individual crosses the Infrared Detection Field, an alert is instantly triggered.
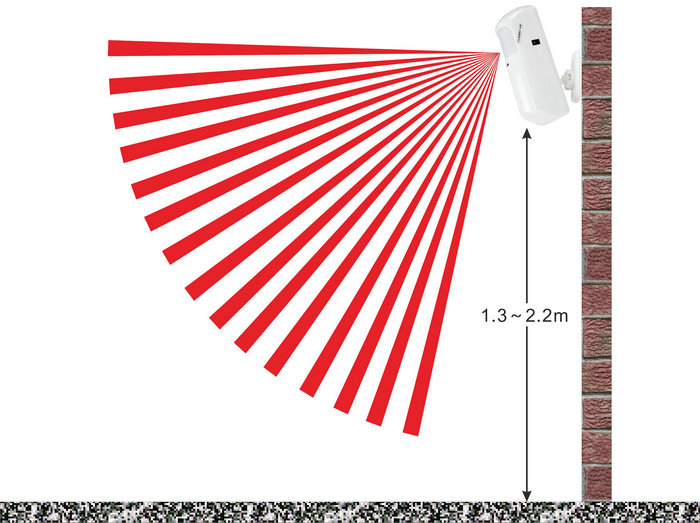
Laser Detection Systems: Create a Monitored Area using Laser Beams; any object crossing the Laser Beam triggers an alarm.
6. Network Intrusion Detection Systems (NIDS) and Network Intrusion Prevention Systems (NIPS)
In Cybersecurity, NIDS and NIPS play a crucial role in monitoring Network Traffic for potential threats and attacks.
NIDS: Analyzes Network Traffic to detect anomalies and unauthorized activities.
NIPS: Not only detects attacks but also takes immediate action, such as Blocking Malicious Traffic.
Conclusion
Common Intrusion Detection methods include Video Surveillance, Access Control, Sensor-Based Detection (Infrared, Vibration, Motion, etc.), Network Intrusion Monitoring, and AI-Driven Behavior Analysis. These technologies help organizations proactively detect and mitigate potential threats, ensuring the security of both Physical Assets and Digital Information.